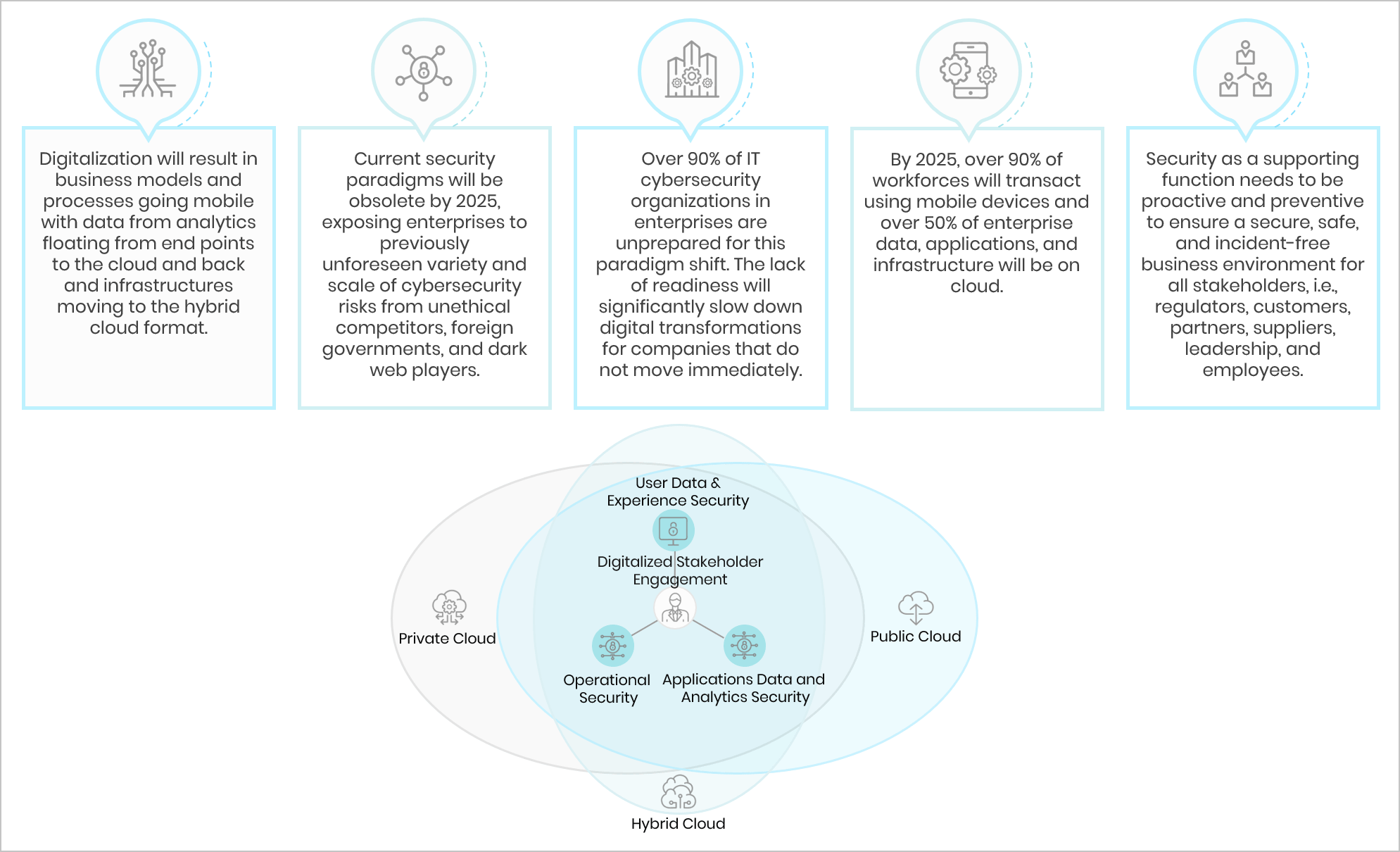
Cloud Vulnerabilities: Challenges With Securing Your Data
The complexity involved in managing disparate solutions securely on the cloud heightens the risk of various security breaches, such as automated hacking. This is made even easier because of the use of default credentials, and easy-to-connect remote access to the cloud.
Protecting your enterprise’s cloud data from threats and vulnerabilities is a complex venture with no margin for error. Our experts are well-versed in cloud strategies and solutions and have conducted numerous successful cloud security engagements.

Our cloud security strategy services will ensure:
Data privacy and encryption in the cloud
In-depth defense with DLP, PAM, anti-malware and ransomware protection tools
Self-determined threat reaction and response
Security analytics
Self-defending, AI-enabled security systems